admin
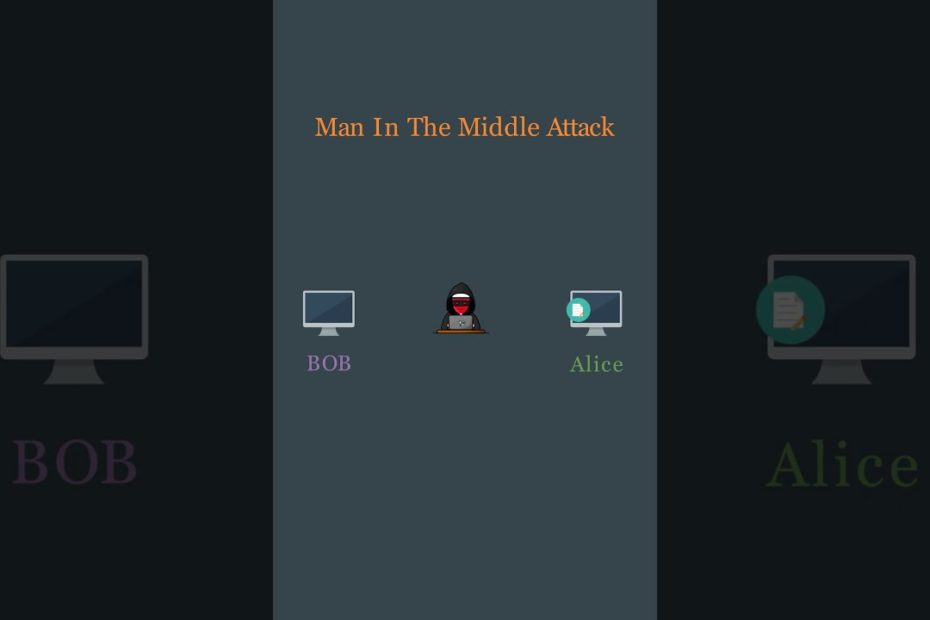
Man-In-The-Middle Attack Explained #hacking #security
Man-In-The-Middle Attack Explained #hacking #security
How to check if your iCloud account has been hacked #shorts
How to check if your iCloud account has been hacked #shorts
Why Kali Linux Is Used For Hacking ? | Kali Linux For Ethical Hackers #Shorts #Simplilearn
Why Kali Linux Is Used For Hacking ? | Kali Linux For Ethical Hackers #Shorts #Simplilearn
This Built-In Feature Prevents Spam, Hacks, and Viruses on the Samsung Galaxy S25 Ultra
This Built-In Feature Prevents Spam, Hacks, and Viruses on the Samsung Galaxy S25 Ultra